4 benefits of an engineering approach to cybersecurity

Chief Creative Officer
It’s common to hear people talk about taking “an engineering approach” to cybersecurity. But what does this actually mean? How does it differ from the legacy model of cybersecurity? And what are the benefits to the enterprise?
The roots of the engineering approach to cybersecurity
The best way to understand the engineering approach to cybersecurity is to look at where it comes from. Broadly speaking, we can say that it stems from three major developments—both within cybersecurity and also in tech generally:
The growth of DevSecOps: The days of “security as an afterthought” are ending. Enterprises and developers now realize that security needs to be considered in every stage of the software development lifecycle. And this has caused a philosophical shift in tech: increasingly, security is seen as a process rather than a feature.
The rise of infrastructure-as-a-service: The success of AWS and other IaaS providers shows that it’s possible to simply give builders the tools they need to do their work, rather than trying to offer ready-made solutions to fit every use case. The benefits of a self-service, scalable, and API-first approach to technology are clear (and proven).
A maturing cybersecurity industry: Cybersecurity has grown up. The industry today is led by people with decades’ worth of experience. The available tooling is powerful and diverse. There is a new level of talent, skill, and specialized knowledge in the market. Because of this, today’s security teams are capable of improving an organization’s cybersecurity posture through testing and iteration—and of building their own, custom tools when needed.
The engineering approach defined
Putting the above factors together, the engineering approach to cybersecurity can be defined as cybersecurity accomplished using the tools, techniques, and methodologies of software engineering.
Specifically, this means:
An emphasis on testing and validation to ensure provable security
The practice of making frequent, iterative enhancements to an organization’s security posture (i.e., security as a process)
Using version control tools to enable rapid changes and the ability to roll back changes if needed
The use of open-source tools and public cloud infrastructure where available
A preference for tools and infrastructure that can be scaled up or down based on need
Building custom tools rather than relying on off-the-shelf solutions when it makes sense to do so
The use of automation to handle provisioning and maintenance when possible
A preference for vendors that offer transparency and control—and ones with a sales culture that supports agility and rapid deployment
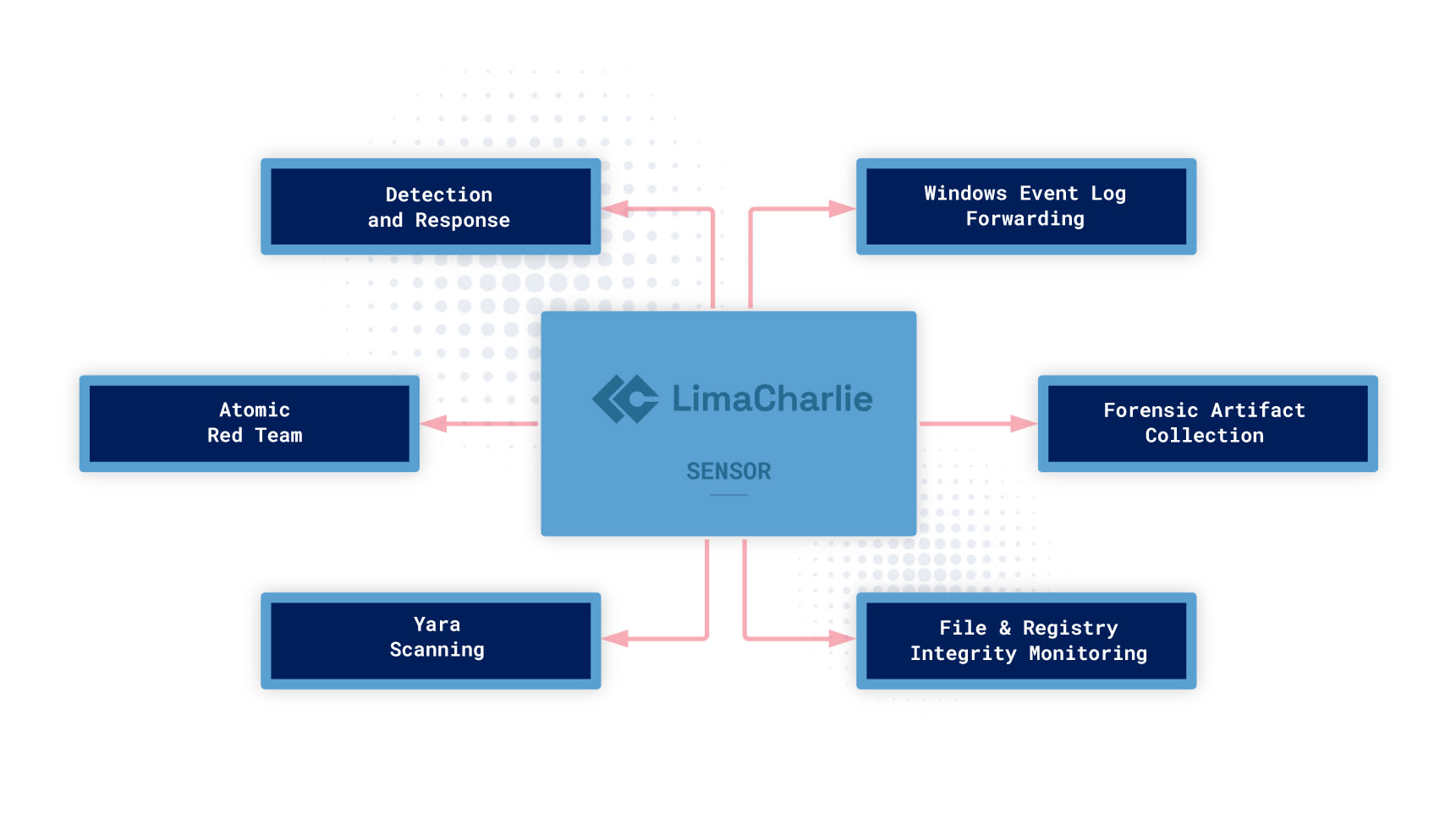
Benefits to the enterprise
This approach to cybersecurity offers a number of business benefits to the enterprise: both to companies in general and also for cybersecurity firms. The best way to understand these benefits is by way of contrast. Let’s look at four major differences between cybersecurity as engineering and the legacy model of security:
1. Proof vs. Trust
An engineering approach to cybersecurity helps to ensure provable security. The tools used are transparent to the security teams using them. And the focus on continuous testing and enhancement means that an organization’s security posture is not assumed—it’s objectively validated.
This is a stark contrast to the way that many large vendors approach cybersecurity: namely, via black-box solutions and an attitude of “just trust us, you’re safe.”
Benefits: Companies know what they’re covered against—rather than having to take vendors at their word. This helps enterprises estimate and manage risk more effectively, something that is especially important in industries with strict compliance and liability requirements.
2. Iterable vs. Static
The tools and methodologies used in cybersecurity engineering enable an iterative approach to security: security as a process. This is because they are, quite literally, designed around the assumption that change is inevitable, and will likely be frequent.
Legacy approaches, on the other hand, tend to treat security as a feature, or a commodity. The end result of this kind of thinking often looks a bit like an attempt to build a perfect wall in the hope that it will hold. Many large vendors reinforce this model by requiring customers to get their help before making changes to a deployment.
Benefits: In today’s constantly shifting threat landscape, agility is essential to good security. But beyond the cybersecurity benefits, there are some important business benefits as well. For one thing, tools built for change help to future-proof a business against the unforeseen: emerging cybersecurity challenges, new regulatory requirements, or just a change in course dictated by the C-suite. In addition, these tools allow firms to make better use of their skilled personnel—for example, by implementing advanced security disciplines such as detection engineering. For some use cases, such as DFIR, working with agile, engineering-first tools brings direct competitive advantages as well: namely, faster response times and the ability to offer attractive service-level agreements.
3. Customizable vs. One-size-fits-all
The engineering approach to cybersecurity is aimed at builders. This is why we often compare LimaCharlie to a box full of Lego blocks for cybersecurity professionals: We give you the tools, capabilities, and infrastructure…and you build whatever you want!
Legacy vendors, needless to say, don’t work this way. Their tools are, well, what they are. They can be modified to a certain extent—but usually with a cumbersome degree of vendor intervention, and almost always at a cost.
Benefits: Businesses that need highly customized solutions are no longer at the mercy of their vendors. They can simply build them: no outside help or permission from a salesperson required. In a maturing cybersecurity industry, that is increasingly feasible, since security teams have the know-how—and the desire—to do this kind of work.
4. Openness vs Protectionism
The engineering approach to cybersecurity is distinguished by the openness of its vendors. The reason for this is obvious: The vendors aren’t competing with their end users—and they see flexibility as one of their key value propositions. This results in greater transparency around the technology itself, as mentioned above. But it’s also reflected in practical ways: scalable, self-service usage; clear, predictable pricing; and usage-based billing.
This is pretty much the opposite of how most large cybersecurity vendors operate. Their business model forces them to push for vendor lock-in, and all that that entails: long minimum contracts, mandatory capacity planning, opaque pricing, and a sales process that sometimes feels more like an audition than a conversation.
Benefits: Working with open, flexible vendors brings a number of business benefits. Projects that would have been cost-prohibitive using traditional vendors—for example, “rip and replace” operations—suddenly become doable. The inherent flexibility of the IaaS model means fewer contract negotiations as well, reducing overhead for executive and finance teams. And engineering-first vendors are often happy to support integrations for open-source tooling, offering companies richer security at lower costs.
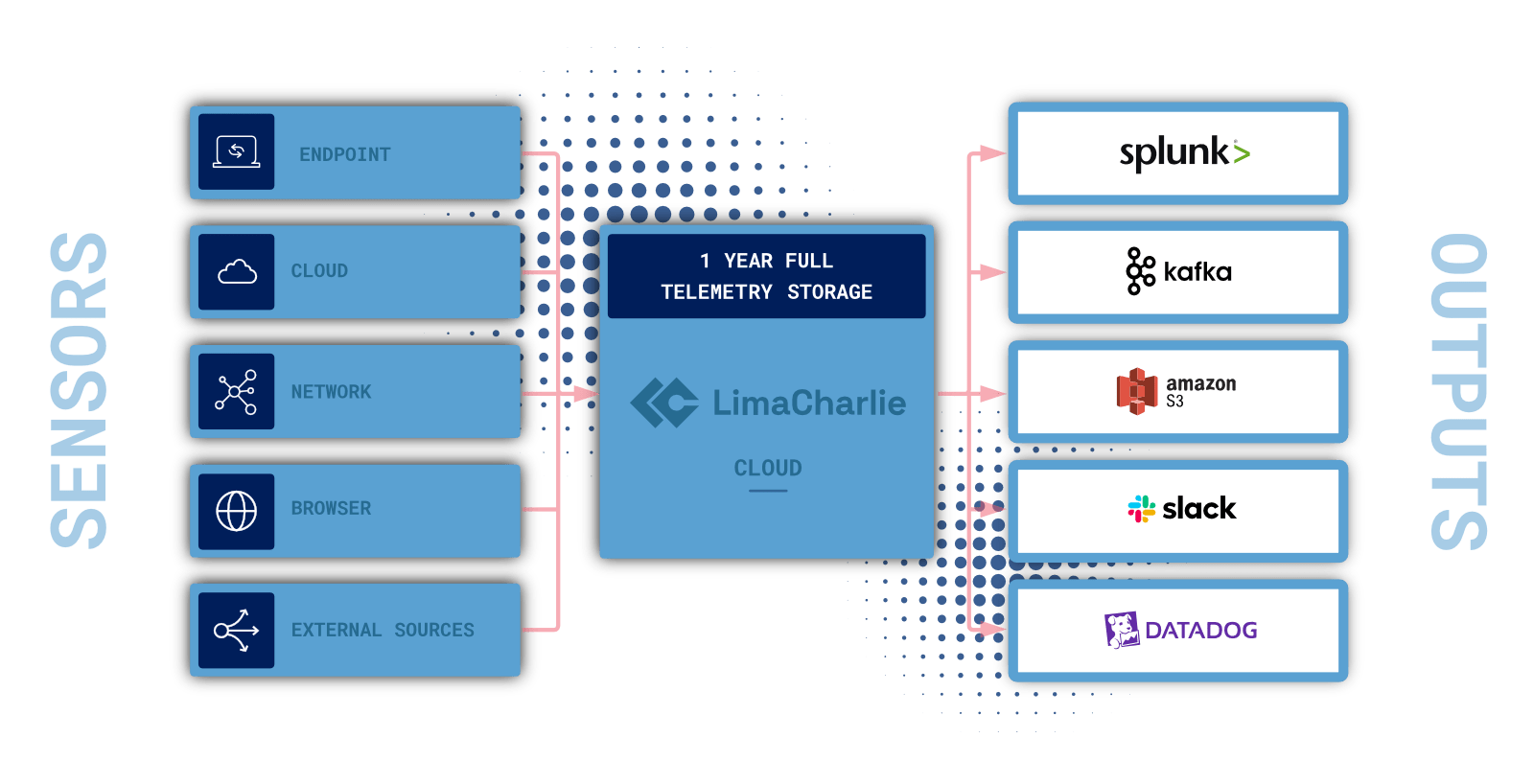
LimaCharlie for cybersecurity engineering
At LimaCharlie, we’re working to make the engineering approach to cybersecurity available to everyone. We offer a free tier that gives users instant access to our suite of powerful cybersecurity capabilities (over 100+ and counting)—no contracts or sales calls required.
We offer integrations for tools like Atomic Red Team in order to help cybersecurity engineers develop testable, provable security. We also offer support for many open-source technologies, such as Velociraptor and YARA and Sigma rules.
Want to learn more? Try LimaCharlie or book a demo today!
440 N Barranca Ave #5258
Covina, CA 91723
5307 Victoria Drive #566
Vancouver, BC V5P 3V6
Stay up-to-date on all things LimaCharlie with our monthly newsletter.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.